A Journey Through Cryptography and Bitcoin
Bitcoin, the first successful decentralized digital currency, represents a culmination of several pioneering concepts in cryptography, digital signatures, and peer-to-peer networks. These developments did not emerge in a vacuum but were instead the result of years of technological advancement. Below, we will trace the key milestones in the history of Bitcoin, beginning with the foundations of public-key cryptography and extending to the digital currency's creation in 2008 and beyond.
1. Public-Key Cryptography (1970s) #
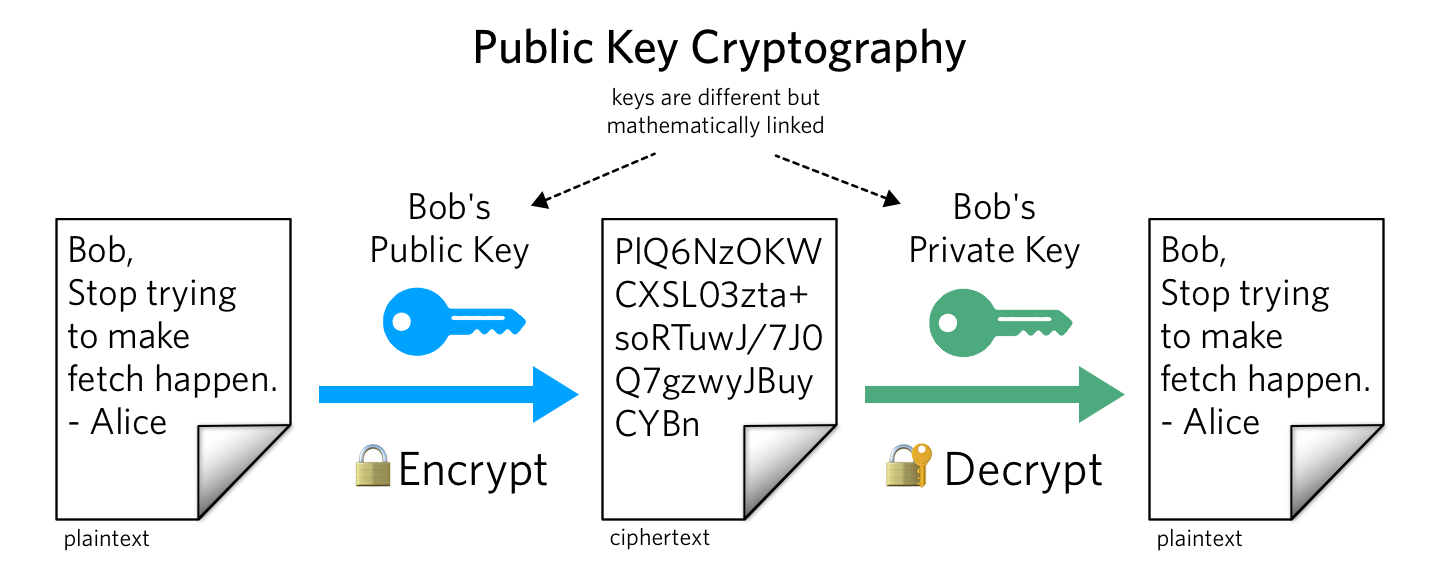
The development of public-key cryptography is one of the most significant achievements in modern cryptography. Public-key cryptography enables secure communications over insecure channels by using asymmetric key pairs (public and private keys). The technology underpins many secure digital systems, including Bitcoin.
Milestone:
- 1976: Whitfield Diffie and Martin Hellman introduced the concept of public-key cryptography, followed by RSA encryption in 1978, which laid the foundation for Bitcoin's security mechanisms.
2. Peer-to-Peer Networks (1990s) #
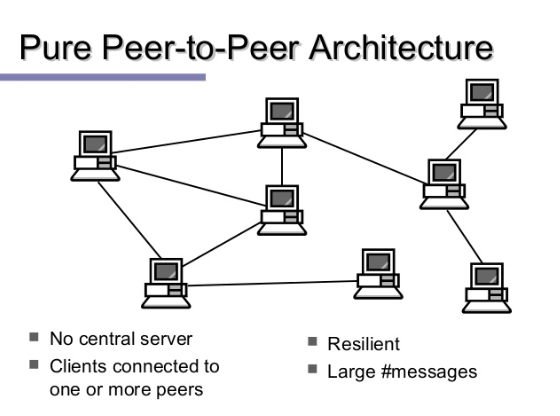
The idea of peer-to-peer (P2P) networks revolutionized the way data is shared and distributed. Instead of relying on a centralized server, P2P networks allow users to share files or resources directly with each other. This idea would become crucial in the development of decentralized systems like Bitcoin.
Milestone:
- 1999: Napster, one of the first mainstream P2P file-sharing services, demonstrated the potential for decentralized networks.
3. Digital Signatures (1970s) #
Digital signatures provide a way to verify the authenticity and integrity of messages or transactions in a digital environment. They are foundational to Bitcoin’s transaction validation, ensuring that only the rightful owner of a Bitcoin address can spend the associated coins.
Milestone:
- 1976: Whitfield Diffie and Martin Hellman also introduced the concept of digital signatures, a key component of public-key cryptography.
4. Cryptographic Hash Functions (1970s - 1990s) #
A cryptographic hash function is a mathematical function that converts an input into a fixed-length string of characters, which appears random. It is a critical element of Bitcoin’s structure, ensuring data integrity and providing proof-of-work in mining.
Milestone:
- 1990s: Cryptographic hash functions like SHA-256 (the one used in Bitcoin) were developed, providing the foundation for Bitcoin’s blockchain.
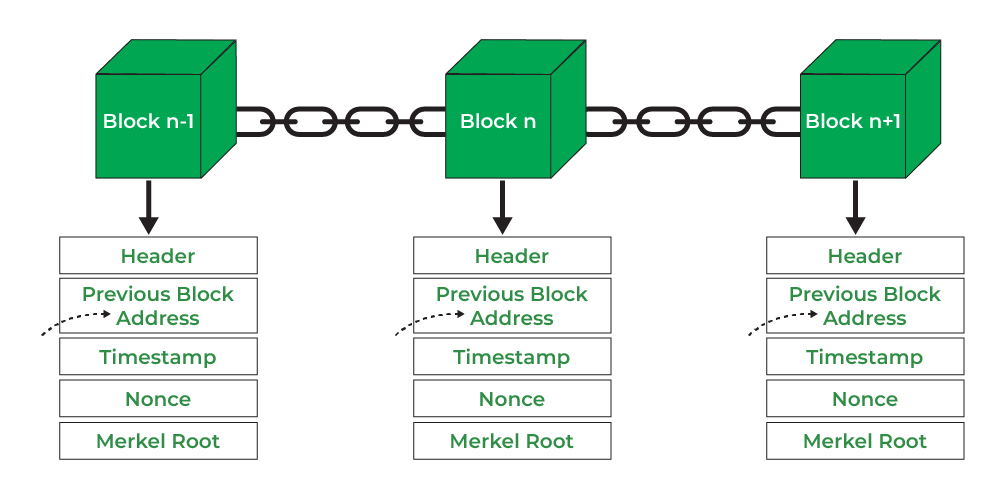
5. Cryptographic Time Stamps (1990s) #
Cryptographic time stamps allow users to prove the existence of certain data at a given time. This concept would later be adapted to form the idea of Bitcoin’s blockchain, where every new block is a timestamped record of transactions.
Milestone:
- 1990: Tim May proposed the use of cryptographic time-stamping, which would later influence Bitcoin's block mining process.
6. Hash Chains (1990s - 2000s) #
Hash chains are sequences of cryptographic hashes that can be used to prove the existence and integrity of a series of data points. In Bitcoin, hash chains are fundamental to the functioning of the blockchain.
Milestone:
- 1997: The concept of hash chains was discussed as a way to create an immutable sequence of data.
7. Proof-of-Work (1990s - 2000s) #
Proof-of-work (PoW) is a mechanism used to secure decentralized networks and incentivize participants to contribute to the network's security. In Bitcoin, miners solve cryptographic puzzles as part of the PoW process to add new blocks to the blockchain.
Milestone:
- 1993: Hal Finney introduced the idea of proof-of-work in the context of digital currencies.
Bitcoin’s Predecessors: A Timeline of Development #
Several important projects laid the groundwork for Bitcoin. Below is a timeline of these key digital currency and cryptographic projects:
Ecash by David Chaum (1982) #
Ecash was one of the earliest attempts to create a digital cash system. It used blind signatures to provide privacy for transactions. Although it did not succeed, it influenced many later projects, including Bitcoin.
E-gold by Douglas Jackson and Barry Downey (1996) #
E-gold was one of the first successful digital currencies. Unlike Bitcoin, it was centralized and backed by gold reserves. However, it failed due to regulatory issues and was shut down in 2009.
Hashcash by Adam Back (1997) #
Hashcash is an early proof-of-work system developed by Adam Back. It was designed as a way to mitigate spam emails by requiring a computational cost (proof of work). It laid the foundation for Bitcoin’s proof-of-work system.
Bit Gold by Nick Szabo (1998) #
Bit Gold was a proposal by Nick Szabo for a decentralized digital currency. It incorporated many elements of Bitcoin, such as proof-of-work and a blockchain-like ledger. Though Bit Gold was never fully implemented, it directly influenced the development of Bitcoin.
B-money by Wei Dai (1998) #
B-money, proposed by Wei Dai, was another precursor to Bitcoin. It introduced the concept of an anonymous digital currency with a decentralized ledger, which was a significant influence on Bitcoin’s design.
RPOW—Reusable Proofs of Work by Hal Finney (2004) #
Hal Finney's RPOW was an early attempt to use proof-of-work to create reusable tokens. This system directly influenced the development of Bitcoin's proof-of-work mechanism.

The Birth of Bitcoin: Technical Aspects and Historical Details #
In 2008, an anonymous individual or group known as Satoshi Nakamoto released the Bitcoin whitepaper, outlining a peer-to-peer electronic cash system. Bitcoin introduced the world to blockchain technology, which uses a decentralized ledger of transactions.
Bitcoin’s major technical components include:
- Decentralization: Bitcoin’s peer-to-peer network ensures that no central authority controls the currency.
- Blockchain: The blockchain stores every transaction in an immutable, timestamped ledger.
- Mining and Proof-of-Work: Miners use computational power to solve cryptographic puzzles and add new blocks to the blockchain.
- Security: Public-key cryptography secures transactions and wallet addresses, while cryptographic hash functions ensure data integrity.